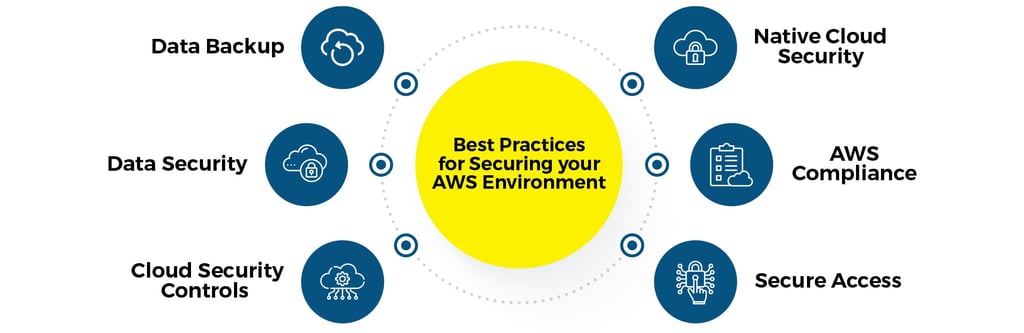
Best Practices for Securing Your AWS Cloud Infrastructure
Enhance AWS security with MFA, strong access policies, encryption, network security, and data backups. Use IAM for precise policies and AWS encryption for data protection. Regularly update measures to stay secure.

In today's digital world, keeping your online information safe is crucial. If you're using Amazon Web Services consulting for your business or personal projects, here are some simple tips to help you keep your cloud setup secure.
Create Strong, Unique Passwords
Your AWS account password is your first line of defense. Make it long, complex, and unique. Avoid using common words or personal information. Consider using a password manager to help you create and store strong passwords safely. Enable multi-factor authentication (MFA) for an additional degree of security. This requires a second form of verification, like a code sent to your phone, making it much harder for unauthorized users to access your account.
Control Access Carefully
Think about who needs access to what in your AWS setupv. Only offer people permissions that are really necessary for their jobs. This helps prevent accidental changes or unauthorized access to sensitive areas of your account.
Keep Everything Up-to-Date
Regularly update your AWS cloud consulting services and any software you're running. Amazon often releases security improvements, and using the latest versions helps keep your setup safer.
Encrypt Your Data
When you store sensitive information in AWS, always encrypt it. Encryption scrambles your data so that even if someone unauthorized gets to it, they can't read or use it without the encryption key.
Monitor Your AWS Account
Keep an eye on what's happening in your AWS account. AWS offers tools that record who did what and when, helping you spot any suspicious activity. Regularly review these logs to catch any potential security issues early.
Secure Your Networks
Use AWS features like Security Groups and Network ACLs to control who can access your cloud resources and what they can do once they're in. Think of this as setting up a secure perimeter around your digital property.
Always Have a Backup Plan
Regularly backing up your data is crucial. It's like having a safety net for your important information. If there's a problem with your main data, you can quickly restore it from your backup. This can save you from losing critical information and minimize downtime. For businesses, this is very important because losing data can cause big financial and operational problems. Set up automated backups in AWS and test your restore process regularly to ensure it works when you need it.
Be Careful with Public Access
Don't make your AWS resources public unless necessary. Keeping things private by default decreases the possibility of unintentional exposure to sensitive data or systems.
Use AWS's Built-in Security Tools
AWS offers a variety of security options to assist safeguard your setup. Services like AWS Config and Amazon GuardDuty can warn you about possible security problems and help you keep your environment safe.
Educate Your Team
If you have a team, make sure everyone understands these security practices. Good security is a team effort, and everyone should know their role in keeping the AWS environment safe.
Conclusion
Securing your AWS cloud doesn't have to be complicated. By following these simple steps, you can significantly improve the safety of your online setup. Remember, good security is an ongoing process. Regularly review and update your security measures to stay protected against new threats.
If you find these steps challenging or want to make sure your AWS environment is secure, think about contacting an AWS consultant. They can offer you tailored advice, helping you follow these best practices the right way while keeping your setup simple and easy to manage.
FAQ's
How can I control access to my AWS resources effectively?
You can control access to your AWS resources effectively by assigning permissions based on the principle of least privilege. Only give individuals the permissions they need to perform their job functions. This helps prevent accidental changes and unauthorized access to sensitive parts of your account.
Why is keeping my AWS services and software up-to-date important?
Keeping your AWS services and software up-to-date is crucial because updates often include security improvements and patches for vulnerabilities. Using the latest versions ensures that your setup benefits from the most recent security measures AWS provides.
How does encryption protect my data in AWS?
Encryption protects your data by scrambling it, making it impossible to read or use without the encryption key. This means that even if unauthorized individuals gain access to your data, they won't be able to understand or exploit it without the key.
How can an AWS consulting partner help me secure my cloud infrastructure?
An AWS consulting partner can provide expert guidance and support to help you implement best security practices effectively. They can tailor security solutions to your specific needs, ensuring your AWS environment is secure and easy to manage.
What are the benefits of using AWS consulting services in India?
AWS consulting services in India offer local expertise and support, helping businesses navigate AWS cloud services efficiently. They provide cost-effective solutions, ensuring your AWS environment is secure, optimized, and compliant with local regulations.